Approval Policy»
Info
Please note, we currently don't support importing rego.v1. For more details, refer to the note in the introduction section.
The approval policy allows organizations to create sophisticated run review and approval flows that reflect their preferred workflow, security goals, and business objectives. Without an explicit approval policy, anyone with write access to a stack can create a run (or a task). An approval policy can make this process more granular and contextual.
Runs can be reviewed when they enter one of three states - queued, unconfirmed, or pending review. Please note if a stack has auto-deploy enabled, then the approval policy will not be evaluated here, and you should use a plan policy to warn which will force the stack into an unconfirmed state and the approval policy will get evaluated as a safeguard.
When a queued run needs approval, it will not be scheduled before that approval is received, and if it is of a blocking type, it will block newer runs from scheduling, too. A queued run that's pending approval can be canceled at any point.
Here's an example of a queued run waiting for a human review - note how the last approval policy evaluation returned an Undecided decision. There's also a Review button next to the Cancel button:

Review can be positive (approve) or negative (reject):
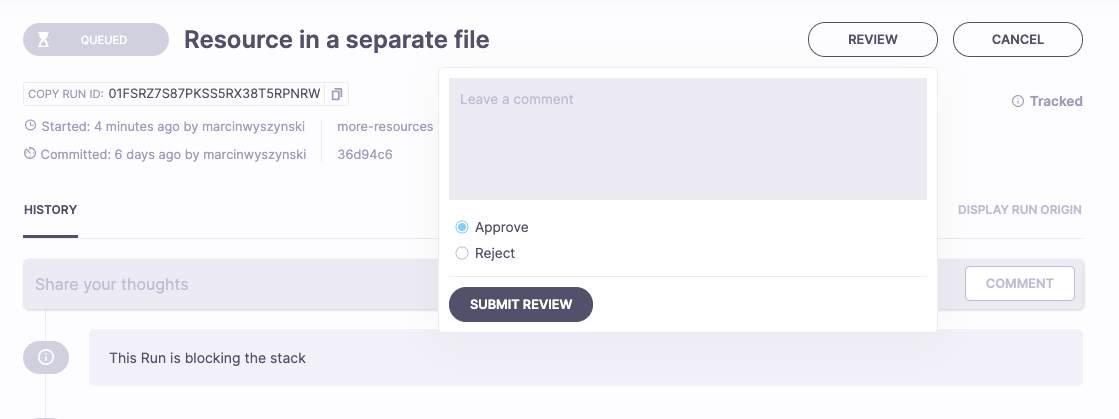
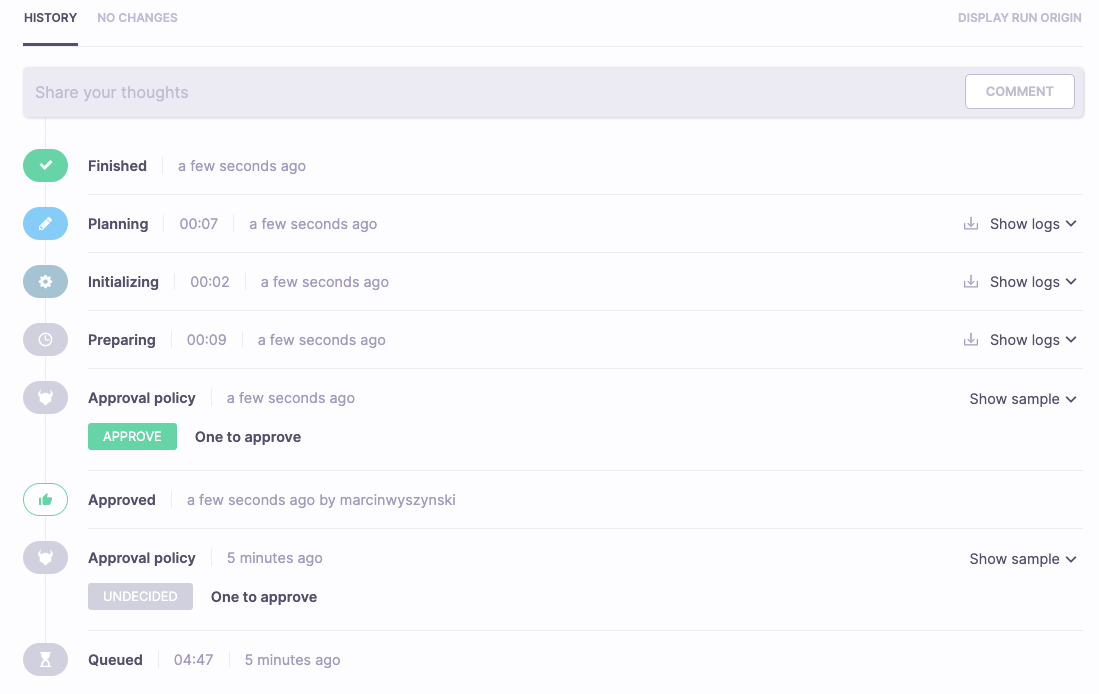
With a positive review, the approval policy could evaluate to Approve, thus unblocking the run:
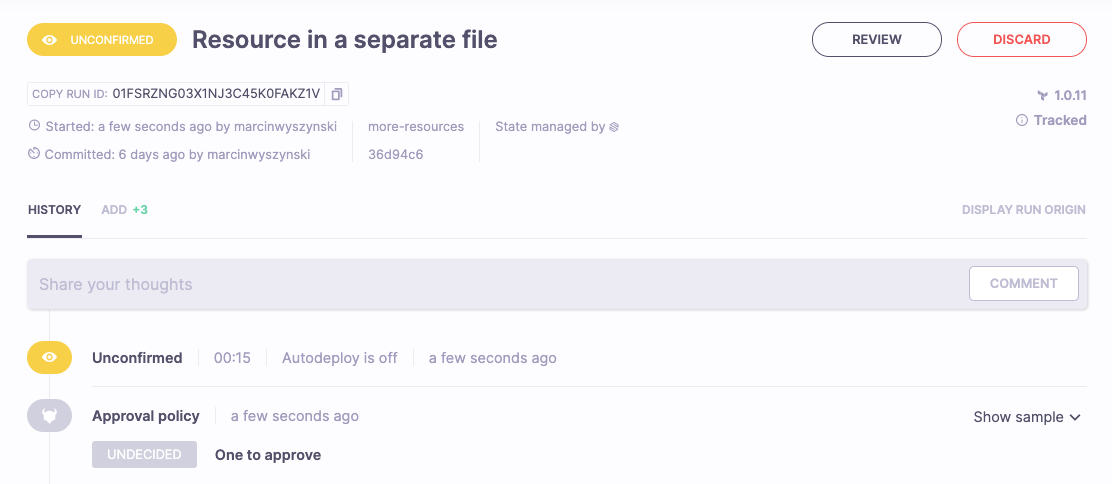
When an unconfirmed run needs approval, you will not be able to confirm it until that approval is received. The run can, however, be discarded at any point:
In principle, the run review and approval process is very similar to GitHub's Pull Request review, the only exception being that it's the Rego policy (rather than a set of checkboxes and dropdowns) that defines the exact conditions to approve the run.
Tip
If separate run approval and confirmation steps sound confusing, don't worry. Just think about how GitHub's Pull Requests work - you can approve a PR before merging it in a separate step. A PR approval means "I'm OK with this being merged." A run approval means "I'm OK with that action being executed."
Rules»
Your approval policy can define the following boolean rules:
- approve: the run is approved and no longer requires (or allows) review;
- reject: the run fails immediately.
While the 'approve' rule must be defined in order for the run to be able to progress, it's perfectly valid to not define the 'reject' rule. In that case, runs that look invalid can be cleaned up (canceled or discarded) manually.
It's also perfectly acceptable for any given policy evaluation to return 'false' on both 'approve' and 'reject' rules. This only means that the result is yet 'undecided,' and more reviews will be necessary to reach a conclusion. A perfect example would be a policy that requires 2 approvals for a given job - the first review is not yet supposed to set the 'approve' value to 'true.'
How It Works»
When a user reviews the run, Spacelift persists their review and passes it to the approval policy, along with other reviews, plus some information about the run and its stack. The same user can review the same run as many times as they want, but only their newest review will be presented to the approval policy. This mechanism allows you to change your mind, very similar to Pull Request reviews.
Data Input»
Info
Note that this is just an example meant for informational purposes (JSON doesn't support comments by design). You can get a sample using the policy workbench.
This is the schema of the data input that each policy request will receive:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 | |
Examples»
Tip
We maintain a library of example policies that are ready to use or that you could tweak to meet your specific needs.
If you cannot find what you are looking for below or in the library, please reach out to our support and we will craft a policy to do exactly what you need.
Two approvals and no rejections to approve an Unconfirmed run»
In this example, each Unconfirmed run will require two approvals - including proposed runs triggered by Git events. Additionally, the run should have no rejections. Anyone who rejects the run will need to change their mind in order for the run to go through.
Info
We suggest requiring more than one review because one approval should come from the run/commit author to indicate that they're aware of what they're doing, especially if their VCS handle is different than their IdP handle. This is something we practice internally at Spacelift.
1 2 3 4 5 6 7 8 | |
Here's a minimal example to play with.
Two to approve, two to reject»
This is a variation of the above policy, but one that will automatically fail any run that receives more than one rejection.
1 2 3 4 5 | |
Here's a minimal example to play with.
Require approval for a task command not on the allowlist»
1 2 3 4 5 6 7 8 9 10 11 12 | |
Info
Options for input.run.type include PROPOSED, TRACKED, TASK, TESTING, DESTROY
Here's a minimal example to play with.
Combining multiple rules»
Usually, you will want to apply different rules to different types of jobs. Since approval policies are attached to stacks, you will want to be smart about how you combine different rules. Here's how you can do that in a readable way, combining two of the above approval flows as an example:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | |
Here's a minimal example to play with.
Role-based approval»
Sometimes you want to give certain roles but not others the power to approve certain workloads. The policy below approves an unconfirmed run or a task when either a Director approves it, or both DevOps and Security roles approve it:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | |
Here's a minimal example to play with.
Require private worker pool»
You might want to ensure that your runs always get scheduled on a private worker pool, and do not fall back to the public worker pool.
You could use an Approval policy similar to this one to achieve this:
1 2 3 4 5 6 7 | |
Here's a minimal example to play with.
You probably want to auto-attach this policy to some, if not all, of your stacks.